The Mirai Worm is a seemingly unstoppable piece of malware that targets the garbage-security Internet of Things gadgets that have proliferated through the world; these gadgets then used to deliver equally unstoppable floods of traffic that endanger whole countries.
Because Mirai (and its cousins) use your devices to target other people, you might never even know that your gadget is destroying the world.
For the past week, security researcher Pascal Geenens has been tracking what appears to be a vigilante response to this threat, a competing worm he’s dubbed “Brickerbot,” which infects these insecure IoT devices and renders them permanently inoperable. Brickerbot is mutating fast, with four versions appearing in a week, each more powerful than the last.
Brickerbot appears to be a botnet hosted on thousands of vulnerable gadgets that are spared euthanasia in order that they might serve as executioners.
There are other vigilante botnets competing with it: Hajime has infected at least 10,000 devices, and is a successor, of sorts, to the Wifatch botnet, which shut down vulnerable devices in 2015.
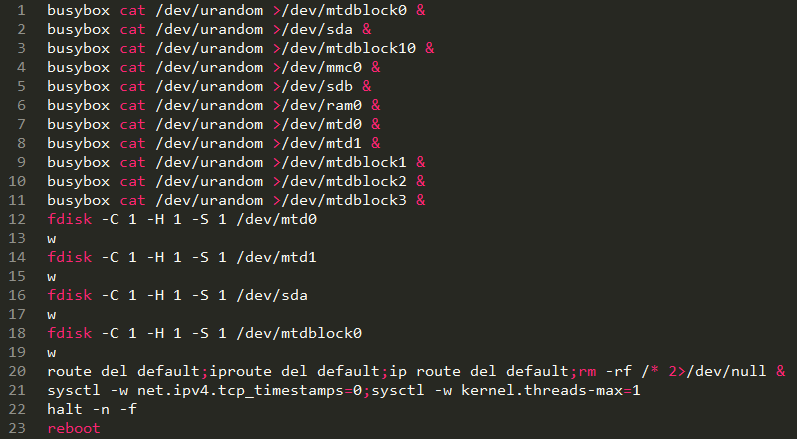
Pascal Geenens, the researcher who first documented what he calls the permanent denial-of-service botnet, has dubbed the fiercest new instance BrickerBot.3. It appeared out of nowhere on April 20, exactly one month after BrickerBot.1 first surfaced. Not only did BrickerBot.3 mount a much quicker number of attacks—with 1,295 attacks coming in just 15 hours—it used a modified attack script that added several commands designed to more completely shock and awe its targets. BrickerBot.1, by comparison, fired 1,895 volleys during the four days it was active, and the still-active BrickerBot.2 has spit out close to 12 attacks per day. “Just like BrickerBot.1, this attack was a short but intense burst,” Geenens told Ars. “Shorter than the four days BrickerBot.1 lasted, but even more intense. The attacks from BrickerBot.3 came in on a different honeypot than the one that recorded BrickerBot.1. There is, however, no correlation between the devices used in the previous attack versus the ones in this attack.”
Commands performed by BrickerBot.3 are identical to those carried out by BrickerBot.1 except for several new ones that put new processes into the background until all resources are exhausted.
Shortly after BrickerBot.3 began attacking, Geenens discovered BrickerBot.4. Together, the two newly discovered instances have attempted to attack devices in the research honeypot close to 1,400 times in less than 24 hours. Like BrickerBot.1, the newcomer botnets are made up of IoT devices running an outdated version of the Dropbear SSH server with public, geographically dispersed IP addresses. Those two characteristics lead Geenens to suspect the attacking devices are poorly secured IoT devices themselves that someone has compromised and used to permanently take out similarly unsecured devices. Geenens, of security firm Radware, has more details here.
[Source:-boingboing]
